.jpg)
Intune
How to Setup the new 'Managed Google Domains' in Intune
By
This is some text inside of a div block.
.jpg)
This is the first blogpost about Managed Google Domains. This blogpost will focus on the steps to setup Managed Google Domains. Other blogposts will focus on Securing Admin accounts for Managed Google Domains, Creating extra Admin Accounts in Managed Google Domains, Setting up multiple bindings for Managed Google Domains (for example for test Tenants).
Introduction
You need Managed Google Domains if you want to manage Android devices in Intune. It establishes a connection between your Intune tenant and Google Play (specifically, a part of Google Play designed for your enterprise, which you can access by going to https://play.google.com/work and logging in with your Managed Google Domain account). This connection—often called a binding—is used for provisioning Google Accounts for your users and distributing apps to your Android devices.
Starting in mid-2024, Google introduced a new way of binding Managed Google Play to your EMM (MDM). This new method is called Managed Google Domains and replaces the previous method, Managed Google Play accounts enterprise, which required you to create your organization’s Google Account manually. This method is still possible, and you can read how to set it up in the blog post on Managed Google Play.
Managed Google Domain has several benefits compared to Managed Google Play accounts enterprise, a couple are:
- You can use a Entra Account that follows your security practices. This account needs a mailbox.
- Google Admin Console is the place where you can manage your admin account, setup federation, add new admin accounts etc.
- Ability to setup SSO for Google Admin Console.
Prerequisites
Create an Entra account that you will use as the Admin account in the Google Admin Console to manage Managed Google Play. Set this up in Entra with your normal admin account security settings. This account needs a mailbox (no other permissions or settings are required). Microsoft’s advice is to log in to the Intune Admin Portal with the same credentials you are going to use for Managed Google Domains. In this scenario, the account also needs permission for Intune. In my testing, I found no difference, and this step is not necessary.
Note: You will need appropriate permissions to add the Google Workspace app to Entra, such as Global Administratoror Application Administrator. Additionally, whether regular users can add applications depends on the settings in Entra, specifically the User Settings for app registration.
How to set this up
- Start by going to the Intune Admin Portal and navigate to:Devices → Android → Enrollment → Managed Google Play.

- Now click ‘Launch Google to connect now’.

- The Google Admin Console will start and prefill with your Intune Admin account that you're currently logged in with. You can change this if needed. Simply fill in the Entra account you want to use for the binding (this account only needs a mailbox).
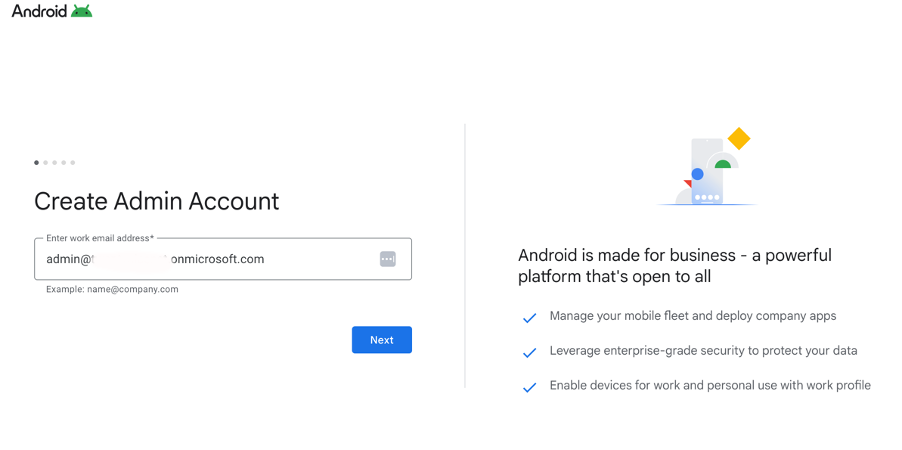
- The system will detect that the account is an Entra (Microsoft) account. Press ‘Sign in with Microsoft’.
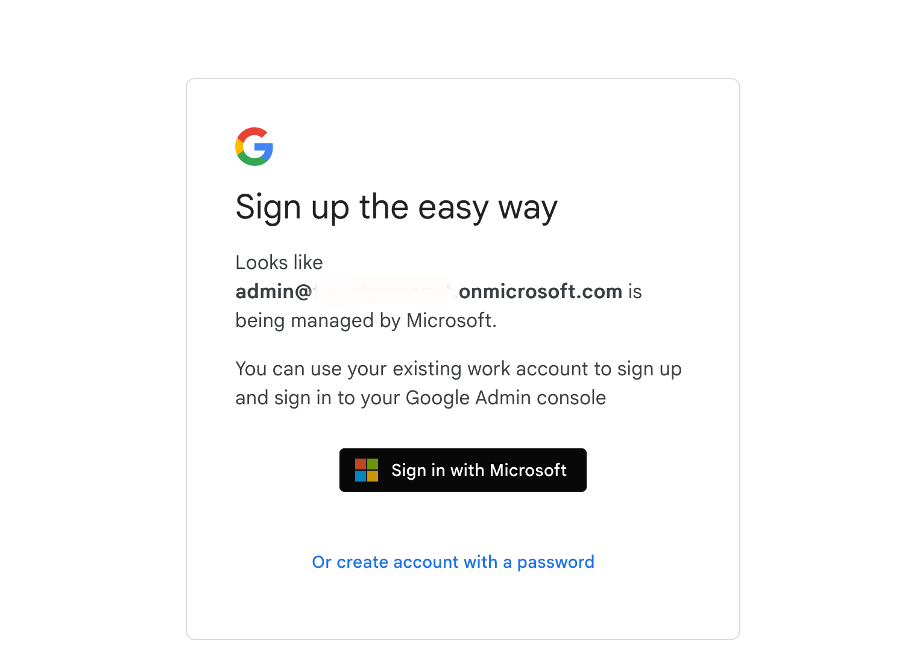
- An Enterprise App called Google Workspace will be created in Entra. This app is used to enable you to log in with your Entra account into the Google Admin Console.
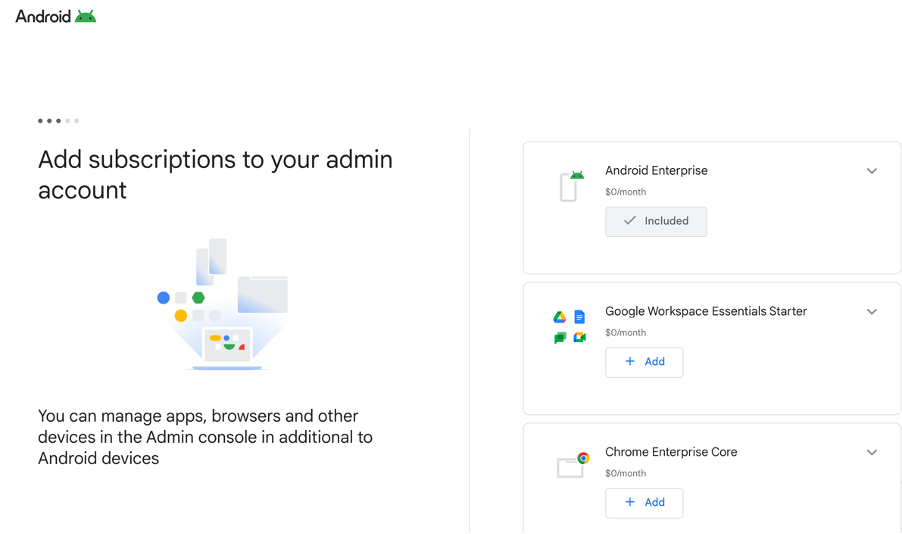
- There are a couple of steps after this that will create the account in the Google Admin Console and establish the binding. When finished, the setup will look like this:
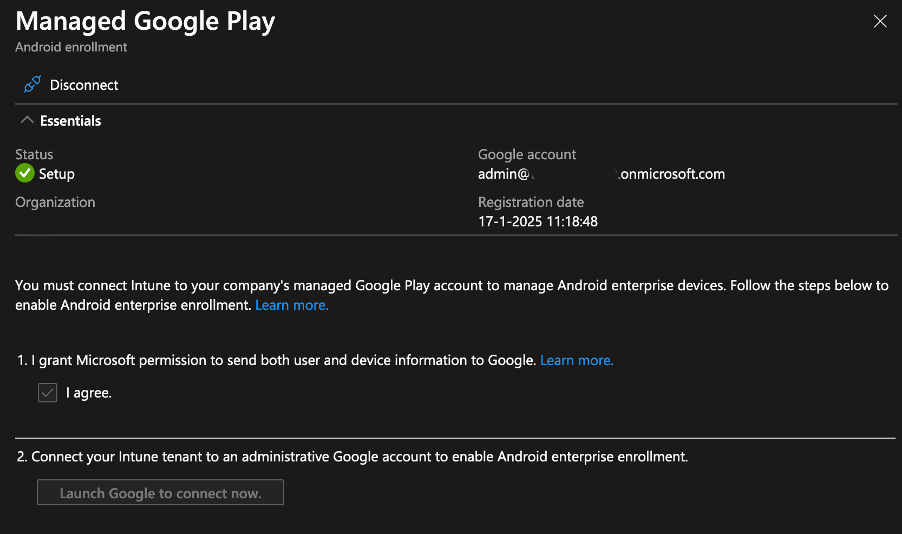
- You are now able to log in to the Google Admin Console by going to https://admin.google.com.
- Navigate to Devices → Mobile & endpoints → Settings → Third-party integrations to find the newly created binding to Intune.

Secure the Google Admin Console with Conditional Access
Once the Google Workspace app has been added to Entra (Azure AD), you can use Conditional Access to secure the authentication process for the Google Admin Console. This enables you to apply additional security policies, such as requiring Multi-Factor Authentication (MFA) or enforcing access only from trusted locations or compliant devices, ensuring that only authorized admins can access the Google Admin Console.
To configure Conditional Access, go to Azure AD → Security → Conditional Access, and create a new policy or edit an existing one (for example if you already have a policy targeted at All Apps) that targets the Google Workspace app. You can specify the conditions under which access is allowed, such as requiring compliant devices or enforcing MFA for sensitive actions in the Google Admin Console.
Conclusion
In this blog post, we’ve walked through the new setup flow for Managed Google Play called Managed Google Domains(introduced in mid-2024). With this new approach, you can integrate your Intune tenant with Google Play, manage your Android devices, and take advantage of enhanced security practices through Entra accounts and the Google Admin Console. Future blog posts will cover additional topics related to managing Google domains, including securing admin accounts and setting up multiple bindings for different environments.






.png)
