
Intune
Enhancing Script Security: Implementing Multi-Admin Approval for Intune Scripts
By
This is some text inside of a div block.

In modern IT environments, allowing a single administrator to deploy scripts—especially those with elevated privileges—can pose serious risks. Whether due to human error, misconfiguration, or insider threats, the unintended consequences of running scripts at scale can be damaging and difficult to reverse. As organizations grow and automate more of their endpoint management, introducing guardrails becomes critical to maintaining control and compliance.
Microsoft Intune offers robust scripting capabilities that enable admins to automate configuration, remediation, and reporting across managed devices. To enhance governance and oversight, Intune now supports multi-admin approval for script deployments. This feature introduces a deliberate approval step, requiring multiple authorized admins to review and approve a script before it can be executed in the environment.
In this post, we’ll explore why multi-admin approval for scripts is important, how to set it up in Intune, and best practices to ensure secure and accountable script management.
Why Multi-Admin Approval for Scripts Is Important
Scripts are powerful tools in modern endpoint management. With a few lines of code, administrators can configure settings, install or remove software, collect diagnostics, or even alter security configurations. While this power is essential for efficiency and automation, it also introduces significant risk:
- High Impact: Scripts can make system-wide changes across many devices simultaneously. A single mistake—like a typo, wrong scope, or unintended logic—can break critical configurations or disrupt user productivity.
- Insider Threats & Misuse: Whether intentional or accidental, a script run by a compromised or careless admin account can lead to data loss, security breaches, or compliance violations.
- Lack of Visibility: Without oversight, it can be difficult for IT or security teams to track what scripts are being deployed, who authorized them, and what impact they have.
Multi-admin approval adds a necessary checkpoint. By requiring a second (or even third) set of eyes before a script is deployed, organizations introduce accountability and reduce the chance of error or abuse. It’s a safeguard aligned with the principles of zero trust and least privilege, helping ensure that changes to managed devices are deliberate, reviewed, and justified.
Prerequisite: Roles and Group Setup for Multi-Admin Approval
To enable multi-admin approval in Intune, your tenant must have at least two administrator accounts—one to initiate the change or creation of a script and one to approve it. This separation is essential for enforcing oversight and reducing risk.
To create or manage access policies, your account must be assigned one of the following:
- Intune Service Administrator
- Azure Global Administrator
- Or a custom Intune role with the "Approval for Multi Admin Approval" permission.
To act as an approver, the account must be part of an approver group linked to the access policy for a given resource type (such as device actions).the approver’s account must have Intune portal access (usually via any Intune-related role like Intune Administrator, or a custom role with portal access).
When you create an Access Policy, the approval process begins immediately—even for the policy you're currently setting up. To avoid delays, make sure a second administrator who is part of the approver group is available and ready to approve the policy as soon as it's submitted.
Configuring Multiple Admin Approval for Scripts
Start by creating an access policy. In the Microsoft Intune admin center, navigate to: Tenant administration>Multi Admin Approval>Access policies. Click Create to start a new access policy.
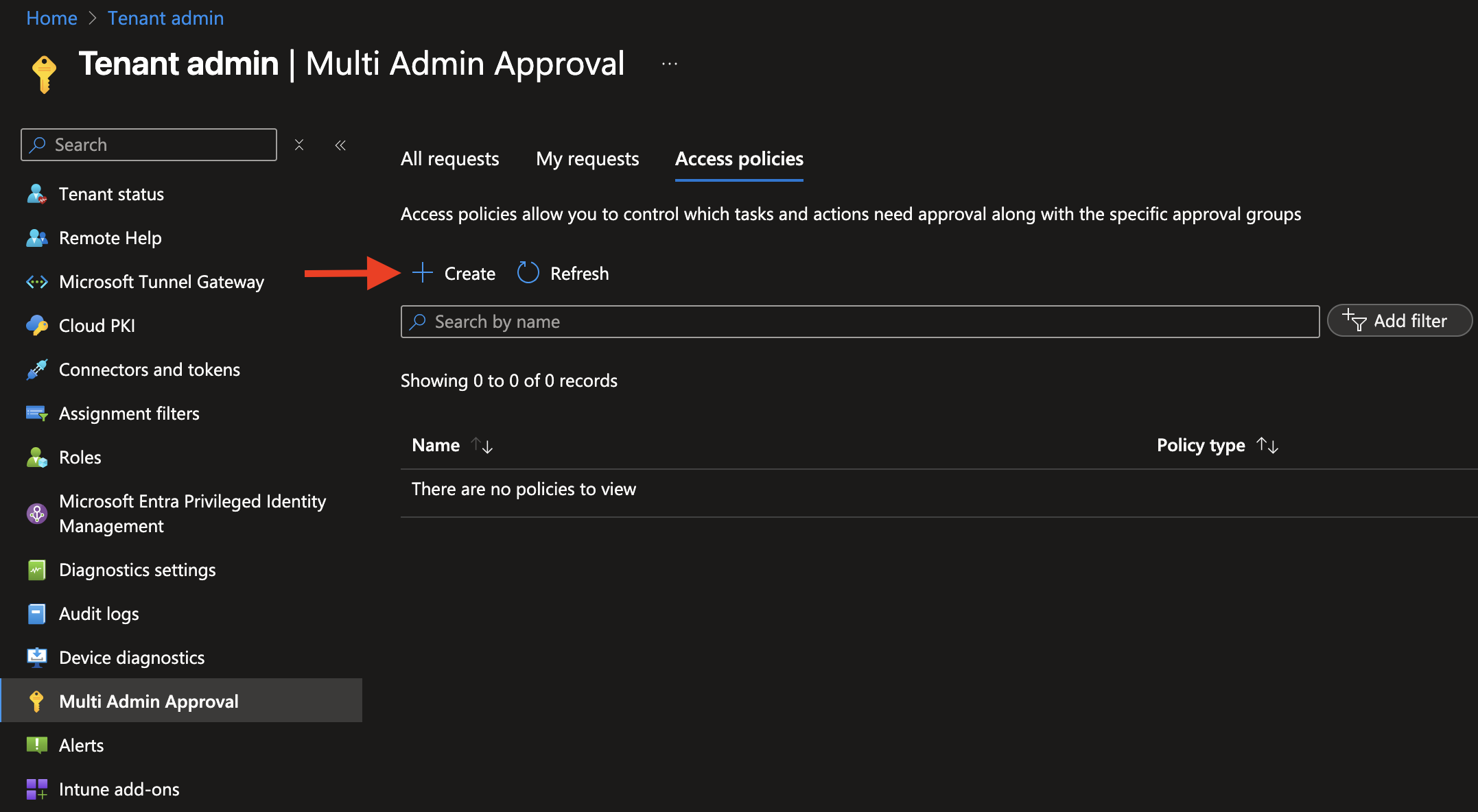
Enter a name for the policy (e.g., "Script Multi-Admin Approval") and an optional description. For Profile type, select Script.
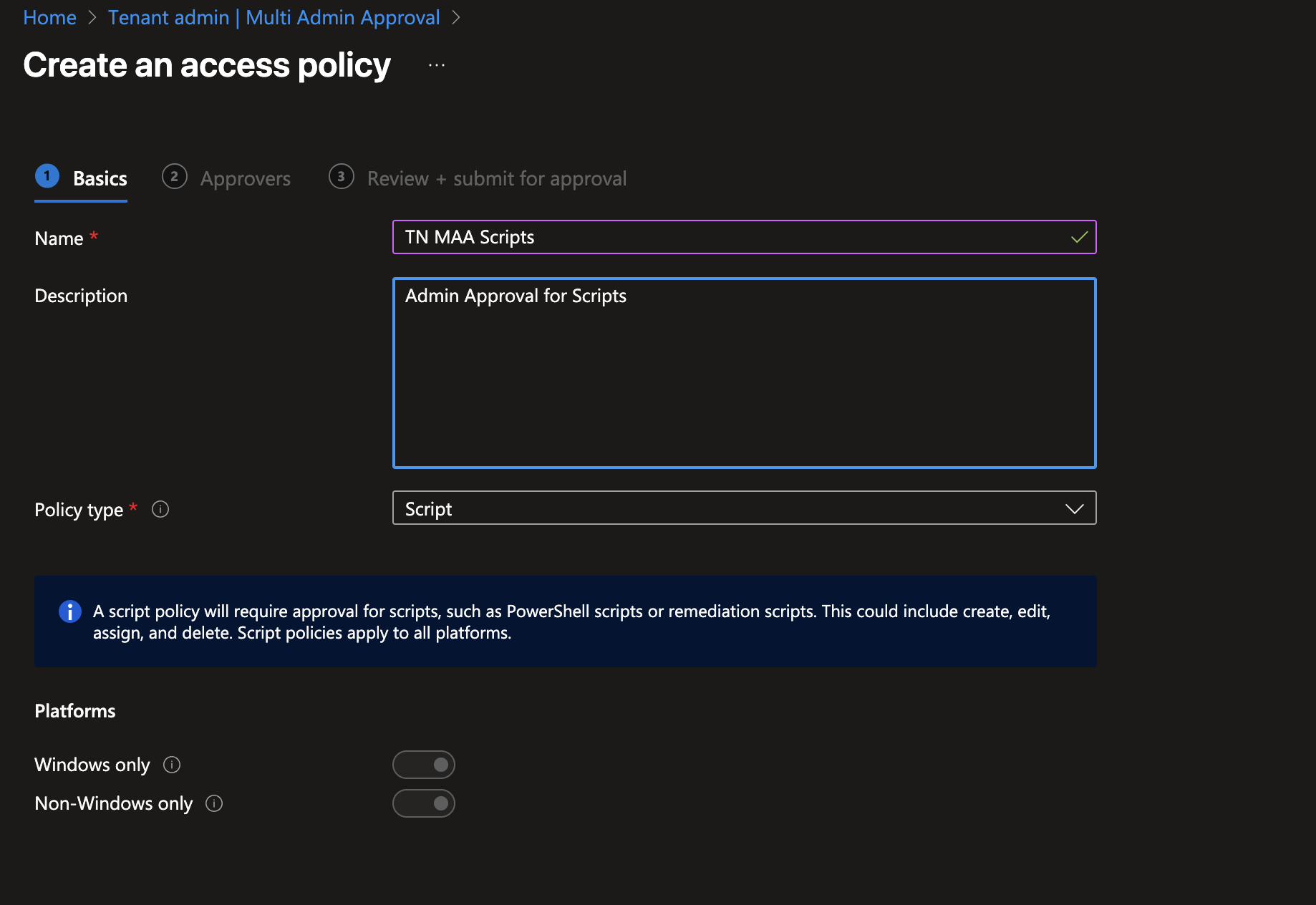
In the Approvers section, select an Entra group. Make sure that everyone who needs to approve the creation and editing of scripts and that needs to approve this Access Policy (see following steps) is a member of this group.
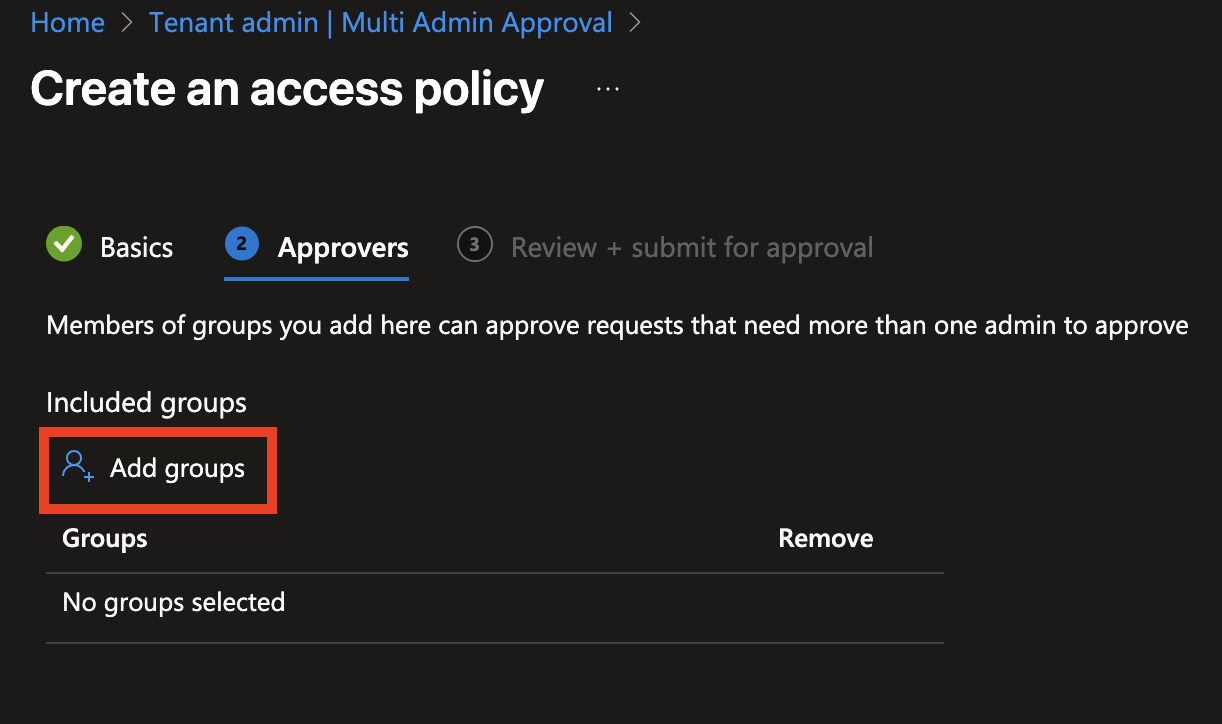
Now you'll see an overview of the policy. The approval process begins immediately after creating the access policy. A second administrator, who is a member of the Approvers group specified earlier, must approve the policy before it becomes active.
There is also a Reason field where you can enter the purpose of the access policy. This helps the approver understand the intent and make an informed decision. Now hit Submit Approval.
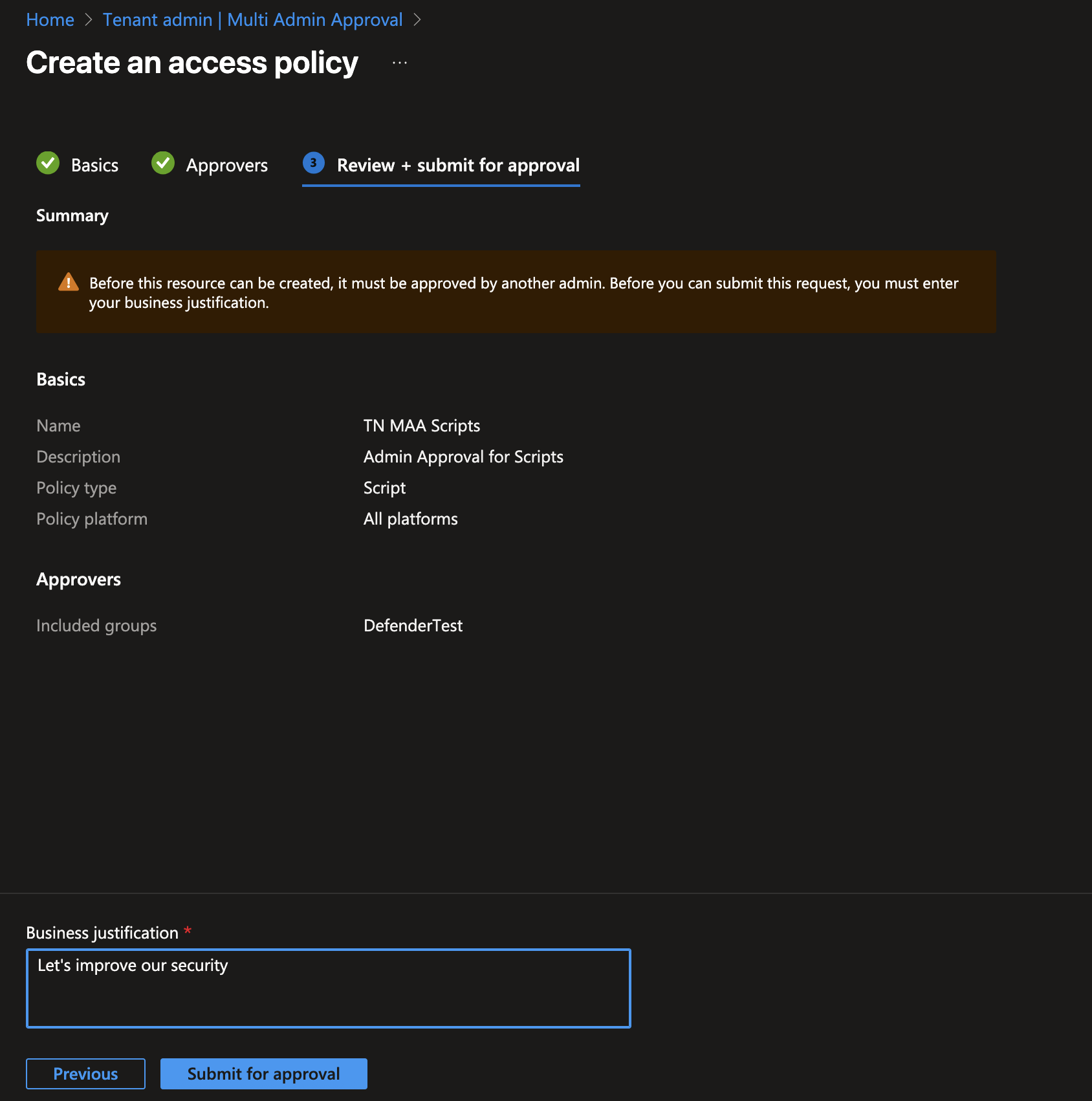
Approve the Access Policy
Now go ahead and make sure that an administrator who is a member of the Approver group you assigned to the access policy logs in (they must also have access to the Intune portal). Then, navigate to Tenant administration > Multi Admin Approval > All requests, and select All requests. The request for the access policy should now be visible.
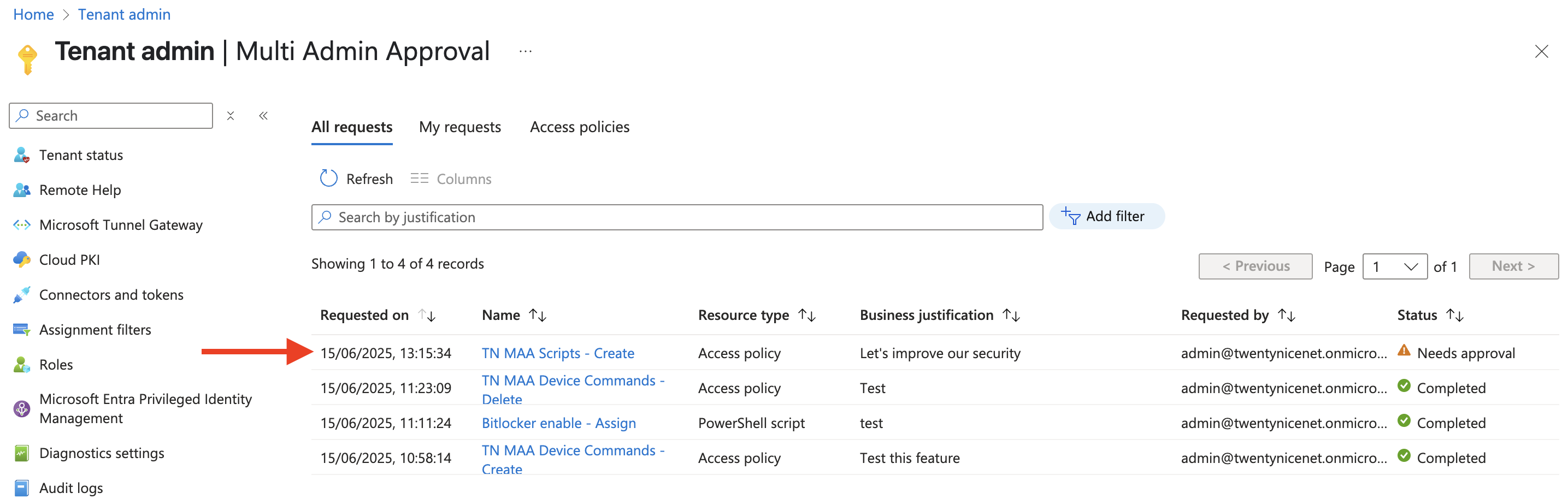
Now have the administrator open the pending request, review the details, and click Approve request.

Activate Access Policy
Now that the approval is finished, have the administrator who created the access policy go back to Tenant administration>Multi Admin Approval>My requests. There, you will find the access policy listed with the status Approved.

Open the access policy by clicking its name, review the approver’s response, and when you are ready to activate the policy, click Complete request.

Example of the Result
Now that everything is configured, let's walk through an example. We have a PowerShell script that we want to deploy to all our devices. As configured in the previous section, Multi-Admin Approval is required for all scripts, so assigning the script to All devices must be approved. Here's the script we want to deploy:
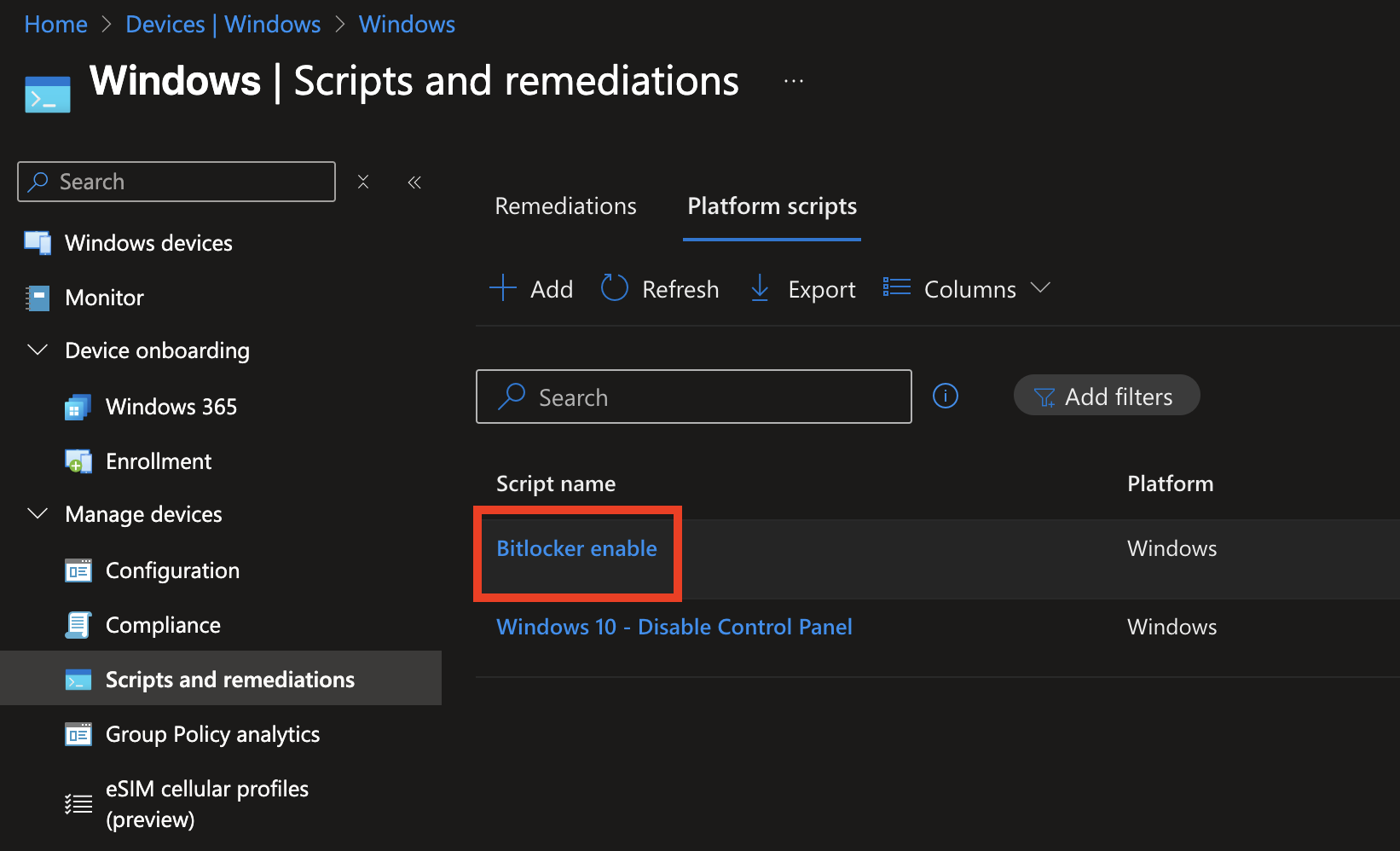
Now assign the script to All devices. You'll notice a new button: Review + submit for approval.
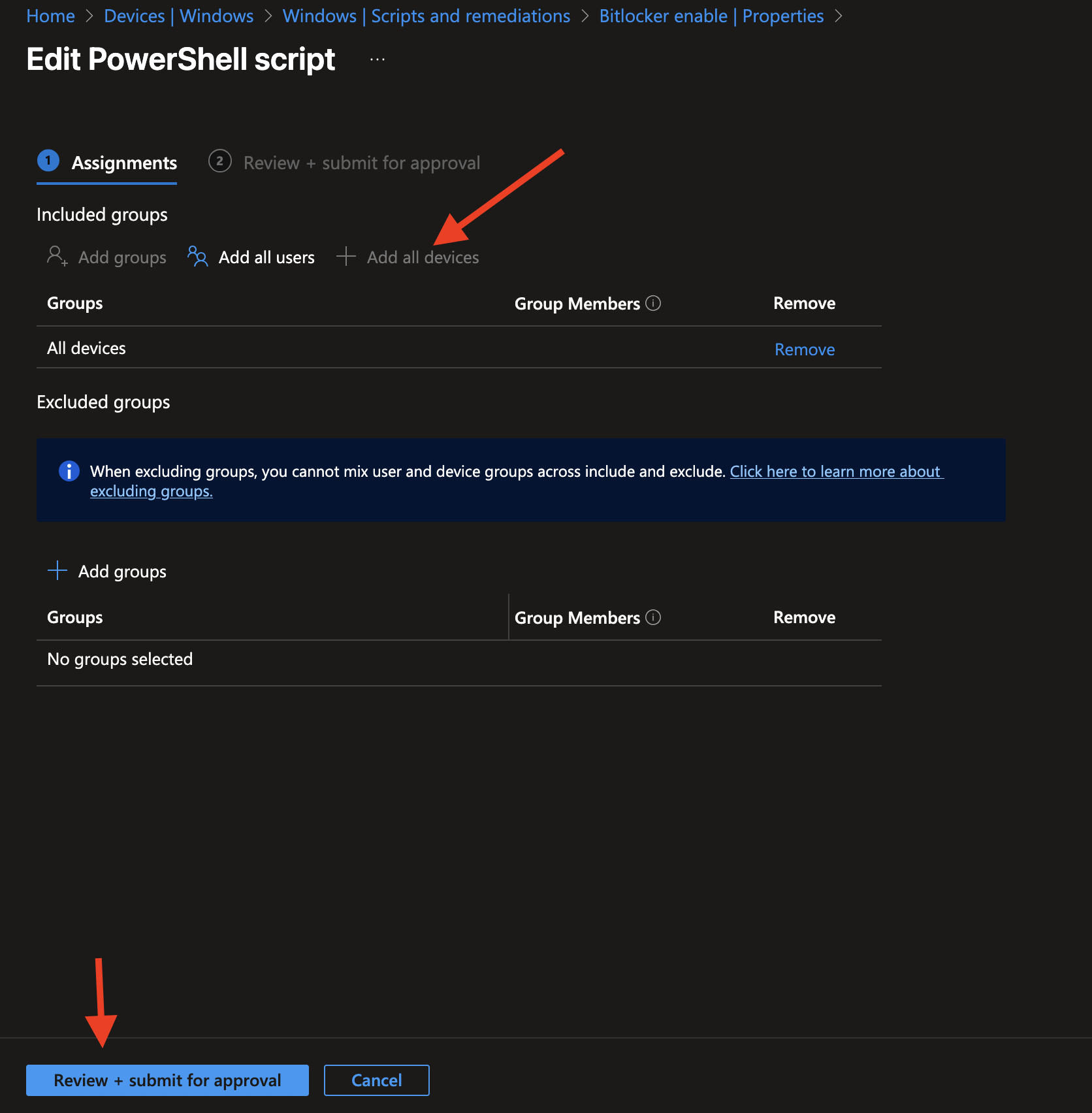
You’ll be presented with an additional screen where you need to provide a business justification for this action. This helps with auditability and gives the approver context for the requested change.Now, click Submit for approval.
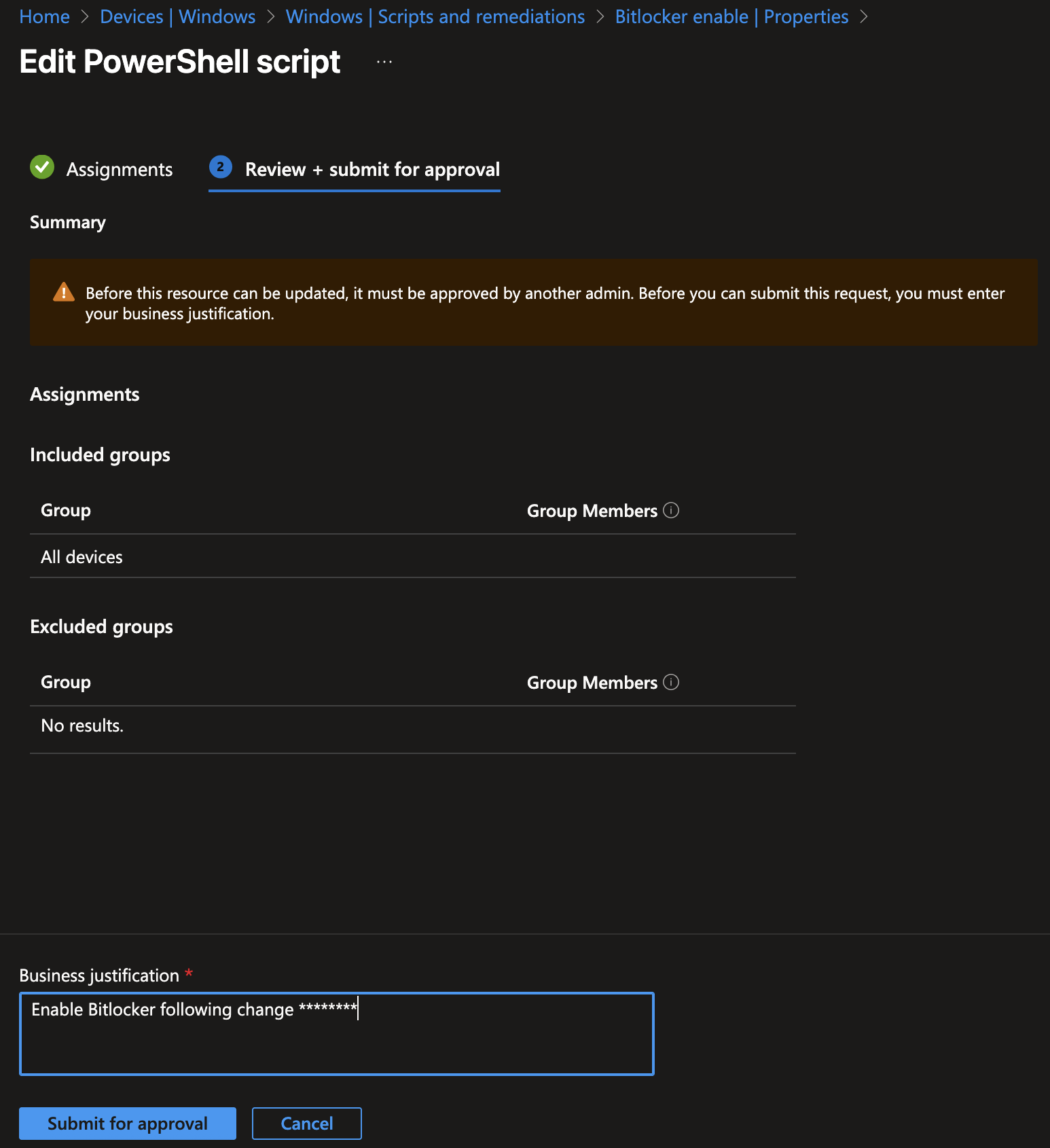
Now switch to another administrator who is an approver, as discussed in the previous section. In the Multi Admin Approval section, the request will be visible.
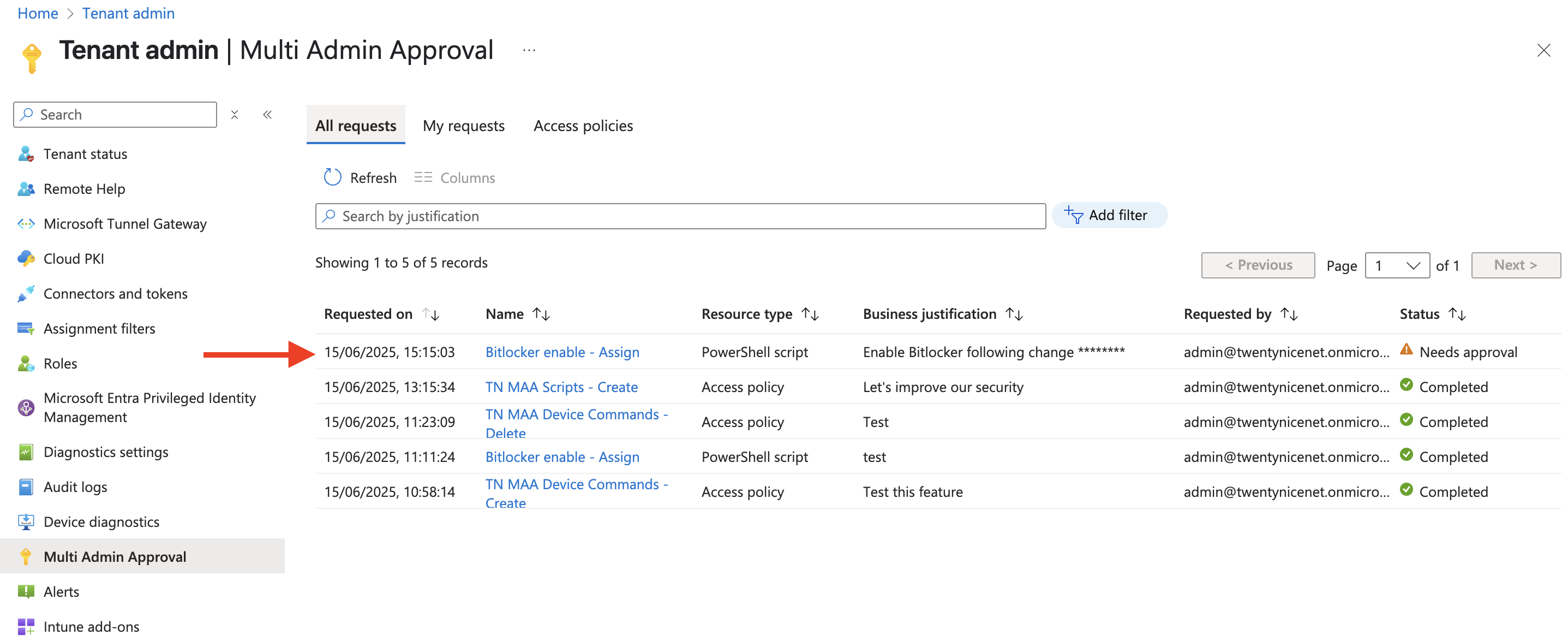
When the request is opened, the approver can review the change and add an optional note for the requester and for audit purposes. The approver can then click Approve request.
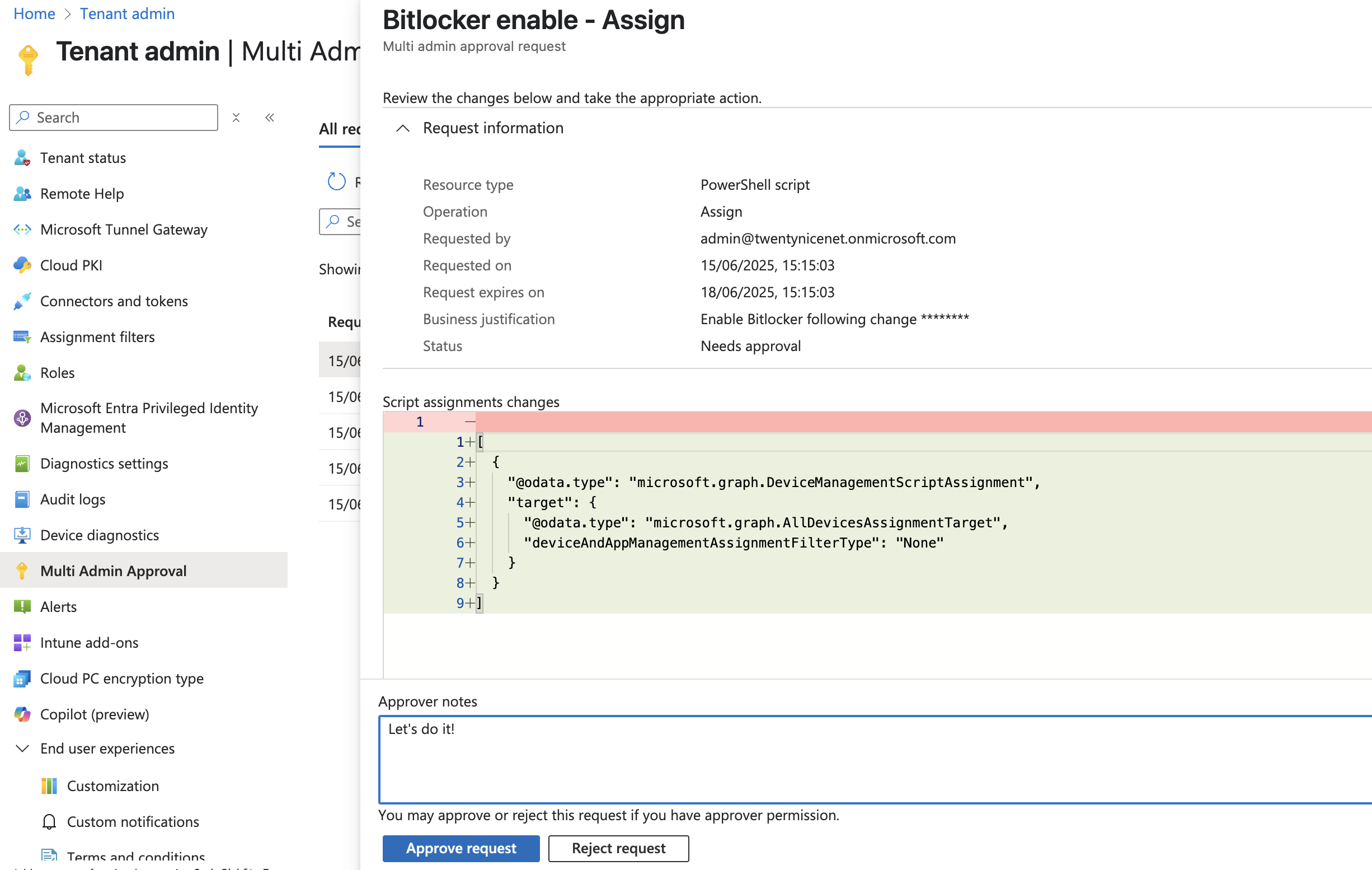
Now switch back to the administrator who requested the change. The Complete request button is now available. Clicking this button finalizes the change—in our example, it completes the script assignment to the group.

Improved Audit Trails and Visibility
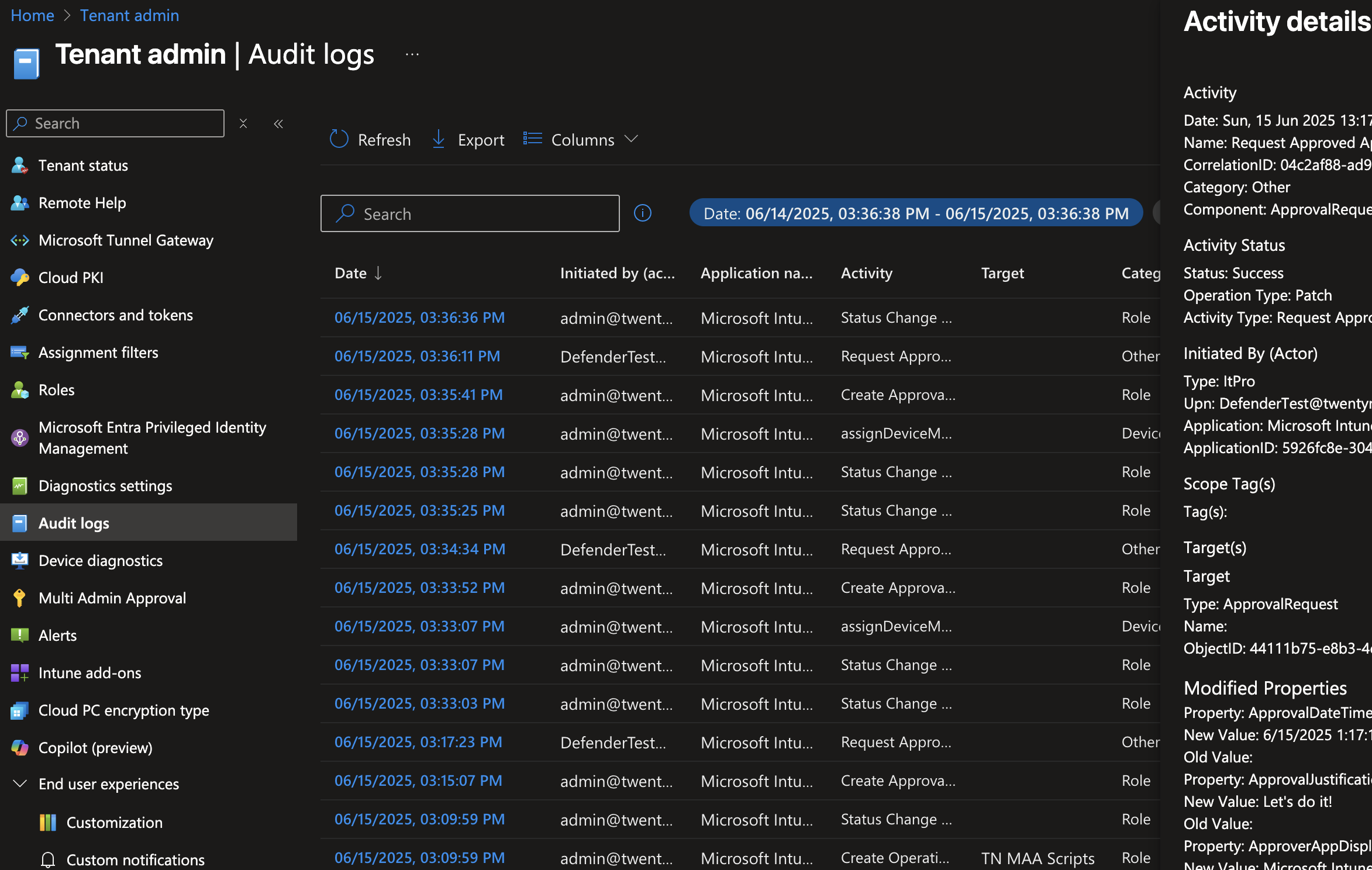
Multi-Admin Approval significantly enhances audit trails by introducing a clear, traceable approval workflow for high-impact changes. Every action—such as creating access policies, submitting requests, providing justifications, and granting approvals—is logged with user identities, timestamps, and optional comments. This level of transparency strengthens accountability and simplifies compliance reporting.
You can view these audit records in the Microsoft Intune admin center by navigating to Tenant administration > Audit logs. There, you’ll find detailed entries that help you track who requested, approved, or completed actions, providing a comprehensive view of change history for review and auditing purposes.
Conclusion: Strengthen Security with Multi-Admin Approval
Implementing Multi-Admin Approval for scripts in Intune adds a critical layer of governance and reduces operational risks by enforcing multiple authorized approvals before executing impactful changes. This process not only mitigates errors and insider threats but also ensures detailed, auditable records of all actions — essential for compliance and security monitoring.
Start configuring Multi-Admin Approval in your Intune environment today to enhance control over script deployments and enforce accountability across your administrative teams. Your security posture will thank you! 🔐





.jpg)
.png)
