
Intune
Automate & Secure: How Intune's DDM Ensures Latest iOS Versions on Your Devices
By
This is some text inside of a div block.

Keeping iOS devices up to date is essential for maintaining security, accessing the latest features, and ensuring compatibility with modern apps and services. However, managing updates through traditional Mobile Device Management (MDM) tools has often been complex and inconsistent, especially across large device fleets. Updates could be delayed, fail silently, or require repeated user interaction. To address these challenges, Apple introduced Declarative Device Management (DDM) — a modern, more scalable approach that empowers devices to take a more active role in their own configuration and compliance, including software updates.
Why Declarative Device Management for iOS Updates?
Traditional MDM operates in an imperative model, where the server explicitly tells the device what to do, step by step. This approach is reactive and often requires frequent polling to verify compliance or initiate actions. In contrast, Declarative Device Management (DDM) allows the device itself to evaluate its current state against a desired configuration defined by the MDM. This shift gives devices more autonomy, enabling them to proactively enforce compliance, report their status, and apply updates without constant external prompts.
Core Concepts of DDM for Updates
Apple’s vision for DDM includes empowering the device to manage its own configuration and compliance. For software updates, this means a device knows what update it should be on and can initiate the process independently, reporting its status back to the MDM. Instead of waiting for instructions, the device becomes an active participant in staying up to date, enhancing scalability and responsiveness.
While many organizations use DDM to keep devices up to date with the latest iOS version, the same policy framework can also be used to target a specific version—such as a particular minor or patch release—depending on business needs. In this blog post we will focuss on the policy to enforce the latest version automatically.
Targeting the latest version helps ensure devices receive the newest features and security updates as soon as they become available, reducing exposure to known vulnerabilities. On the other hand, targeting a specific version gives IT more control over rollout timing, allowing for internal testing and validation before deployment. This approach can help avoid compatibility issues with critical apps or workflows but requires more active monitoring to stay aligned with Apple’s release cycles.
How Intune Integrates with Apple’s DDM for Updates
Microsoft Intune leverages Apple’s DDM framework by declaring a desired software update version on supervised iOS devices. Intune sends a declarative update payload, and the device autonomously initiates and manages the update process, checking against Apple’s servers and applying the update when conditions allow. This reduces delays and increases the likelihood of successful, timely updates.
Prerequisites for DDM Updates in Intune
To use DDM for software updates in Intune, the following conditions must be met:
- Device Requirements:
- iOS 15 or later (iPadOS 15+ for iPads)
- The device must be supervised and managed via Apple School Manager or Apple Business Manager
- Licensing:
- Microsoft Intune Plan 1 or higher (typically included in Microsoft 365 E3/E5 suites)
Step-by-Step: Configuring Intune to Enforce Latest iOS Updates via DDM
To begin, sign in to the Microsoft Intune admin center and navigate to Devices > iOS/iPadOS > Configuration profiles. Click on + Create profile, then choose:
- Platform: iOS/iPadOS
- Profile type: Settings catalog
Click Create, and give the profile a clear name (e.g., iOS DDM Update Policy). This will serve as the foundation for applying Declarative Device Management (DDM)-based update settings to your managed iOS devices. Continue to the next steps to define the exact settings.
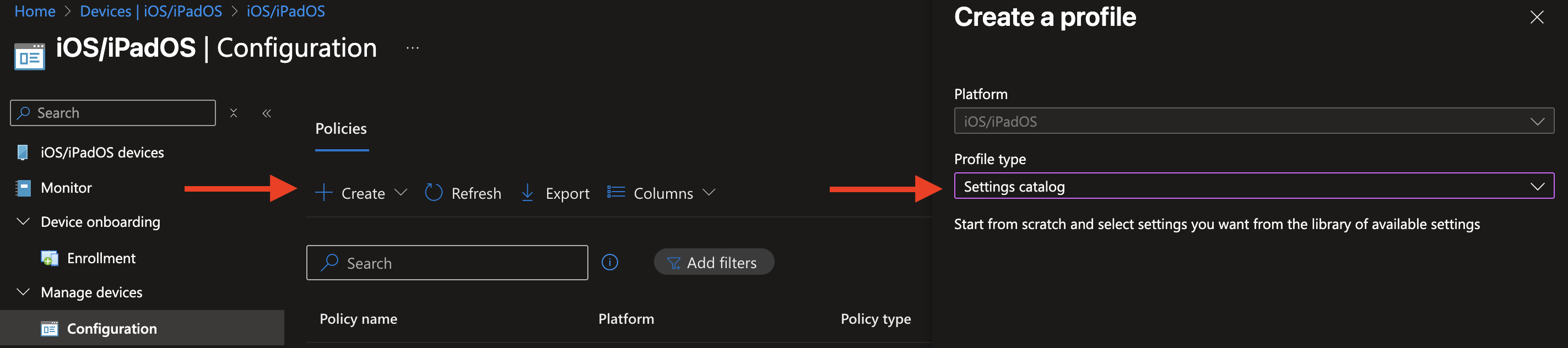
Now click Add settings. Under Declarative Device Management (DDM), you'll find Software Update Enforce Latest. If it’s not immediately visible, you can also use the search bar to look for Software Update.
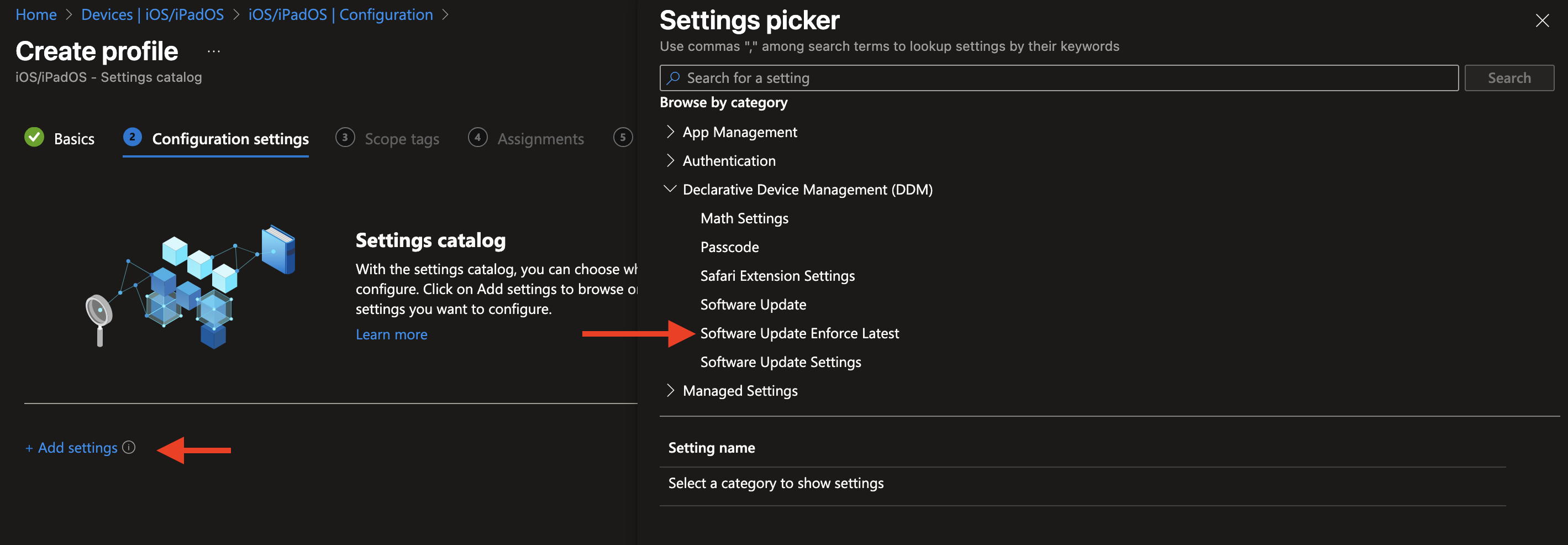
When selected, a new menu will appear below. Make sure to check the box—this will reveal the configuration options in the left column.
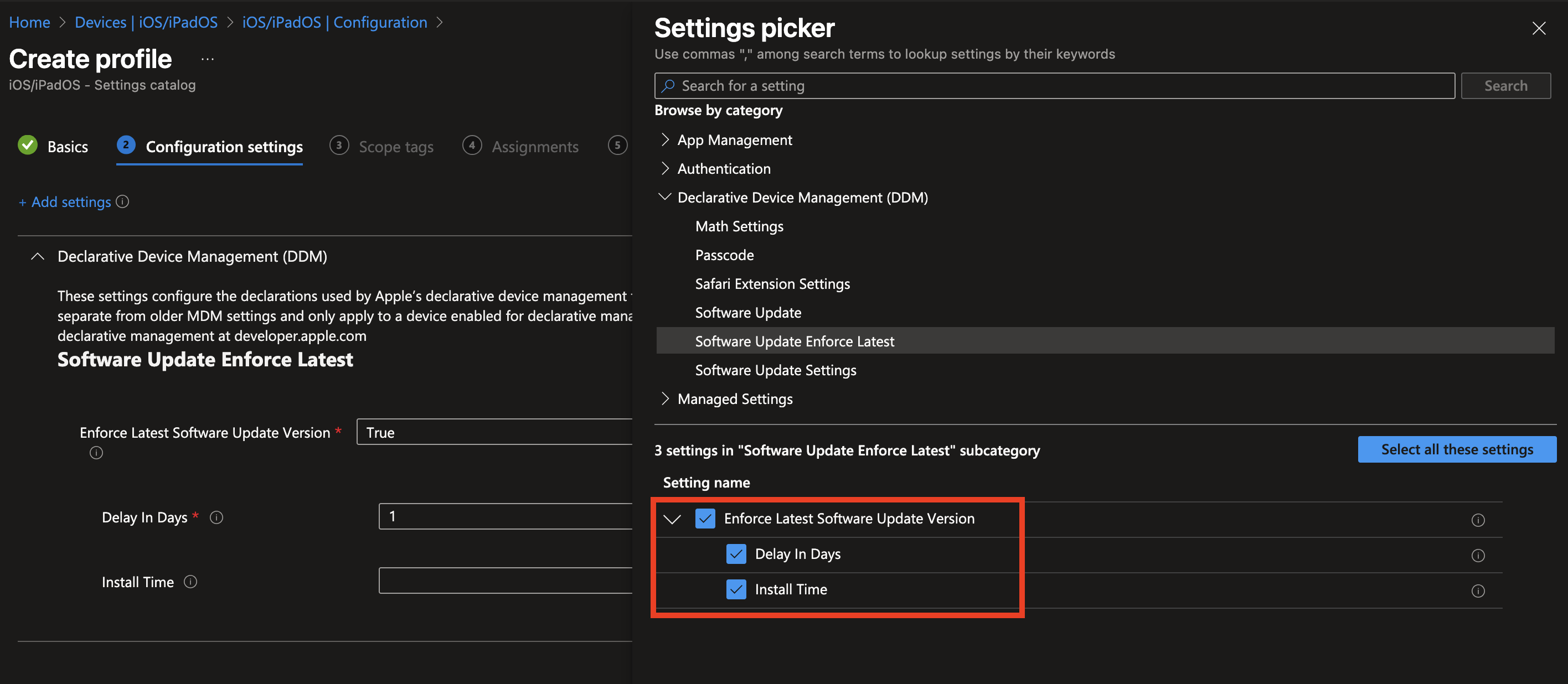
There are two settings to discuss. The Delay in Days setting allows IT administrators to specify how many days should pass before the update enforcement deadline takes effect. This delay period is calculated either from the date Apple officially posts the new update or from the moment the update policy is configured in Intune—whichever event is later. Essentially, this means you can control how soon devices are required to install the update after it becomes available or after your organization decides to start pushing it out. The maximum delay allowed is 90 days, though most enterprises typically set this to around 30 days. Using this delay is a practical way to create a buffer period during which IT teams can perform internal testing, assess compatibility with critical business applications, or prepare communications for end users. This flexibility is especially valuable in enterprise environments where immediate update installation could disrupt workflows or introduce unexpected issues.
Gradual rollout is typically achieved by configuring multiple update policies with progressively increasing Delay in Days settings. Each deployment ring is assigned a specific delay period, so critical or pilot groups receive the update first with a shorter delay, while broader or less critical groups have longer delays before enforcement. This staged approach helps organizations identify and address potential issues early on, minimizing risk and ensuring a smoother update experience across all devices.
The Install Time setting specifies the local device time when update enforcement begins, allowing organizations to control when updates install. While scheduling updates during off-hours is common to avoid disrupting users, many enterprises prefer business hours since users often rely on their devices remotely or at home in the evening—times when unexpected restarts can be problematic. Conversely, off-hours installations can minimize interruptions during peak usage. Ultimately, choosing the best install time depends on understanding your users’ habits and support capabilities to minimize disruption while maintaining timely updates.

Next, you assign scope tags to control administrative access and visibility of the policy. Then, you select the target device or user groups to which the update policy will apply. Finally, you review all the settings and hit create.
What Your Users See: The iOS Update Experience with DDM
Now let’s take a look at what end users will actually experience on their devices. Enforcing updates is always a delicate process—especially when it involves an automatic restart. If users aren't properly informed, there's a real risk of data loss if they’re in the middle of something important. That’s why Apple’s notification system is designed to gradually increase in frequency as the enforcement deadline approaches. The goal is to make the update process as transparent and predictable as possible.
Windows users have grown accustomed to this kind of experience, and with Apple’s structured approach, I believe iOS users will follow the same path. The repeated prompts, clear deadlines, and system-enforced behavior make sure updates don’t come as a surprise—while still giving users time to act on their own terms.
For Apple’s explanation and the latest features, please visit the Installing and enforcing software updates for Apple devices knowledge article.
When a DDM update policy is applied, a clear enforcement deadline is set. With the latest policy configuration, this deadline is determined by a delay—starting from either the moment Apple releases the update or when the DDM configuration is created, whichever comes later. As the device approaches this deadline, users are guided through a tiered notification system that gradually increases in frequency. Notifications are delivered through two primary channels:
- In Settings > General > Software Update
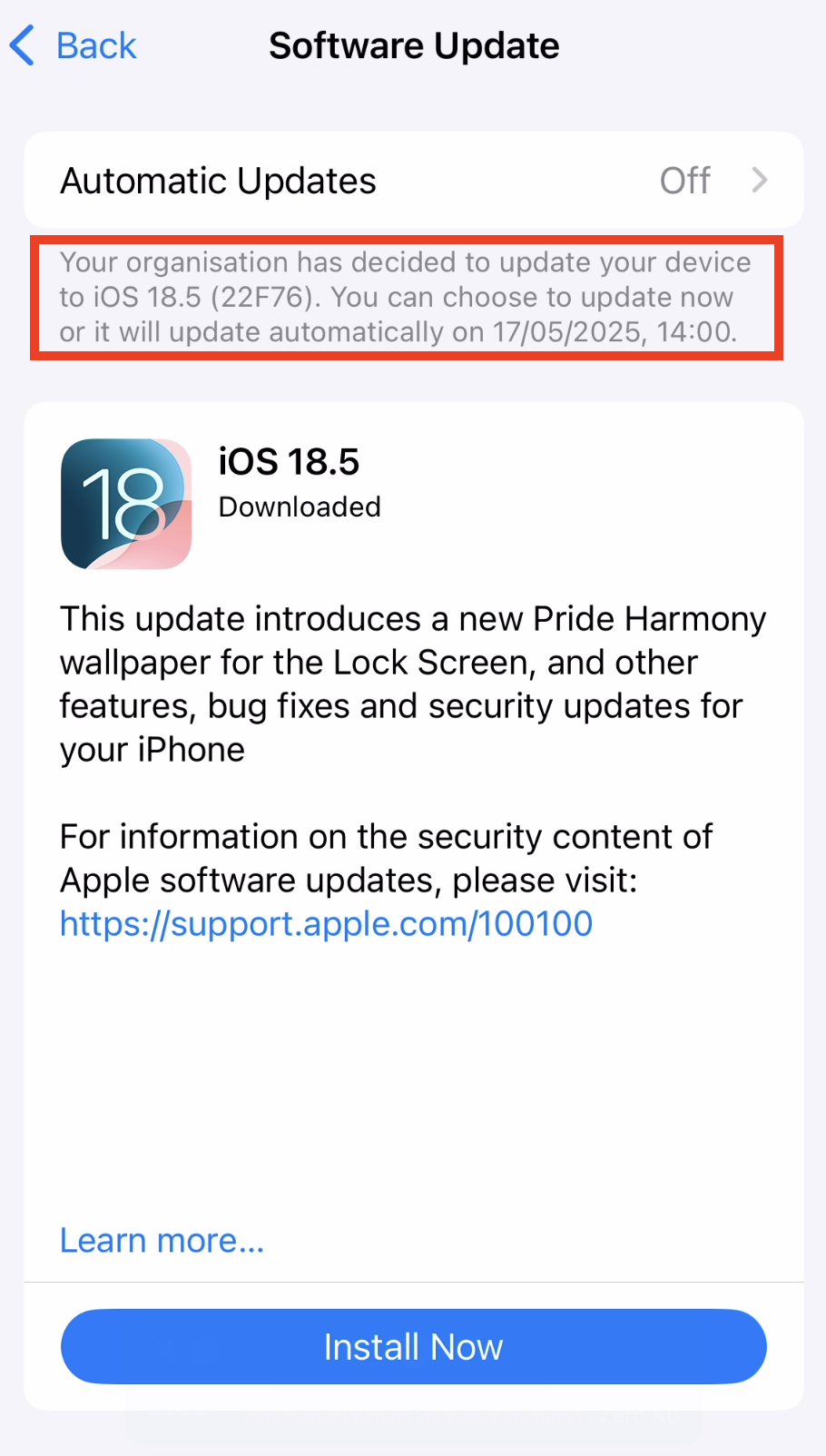
- And in a notification visible in the lockscreen

and as prompt:
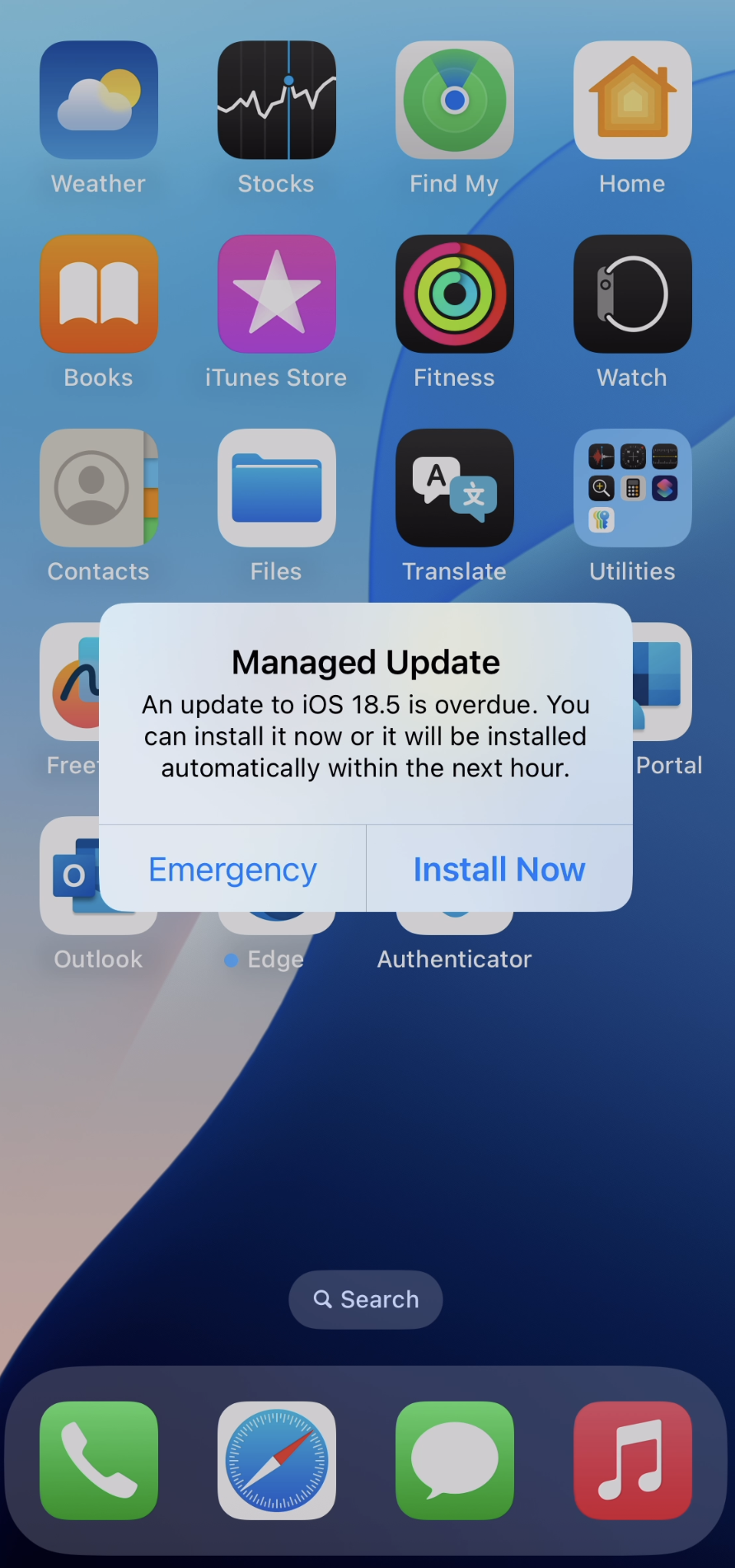
The update in Settings will remain visible until the update is successfully installed. After installation, the system will notify the user that the device is up to date according to company policy. In Settings, the available install options typically include "Install" and "Try Tonight," but within the final 24 hours before the deadline, only the "Install" option is shown. Notifications will gradually increase in frequency as the deadline approaches. Please refer to this picture:
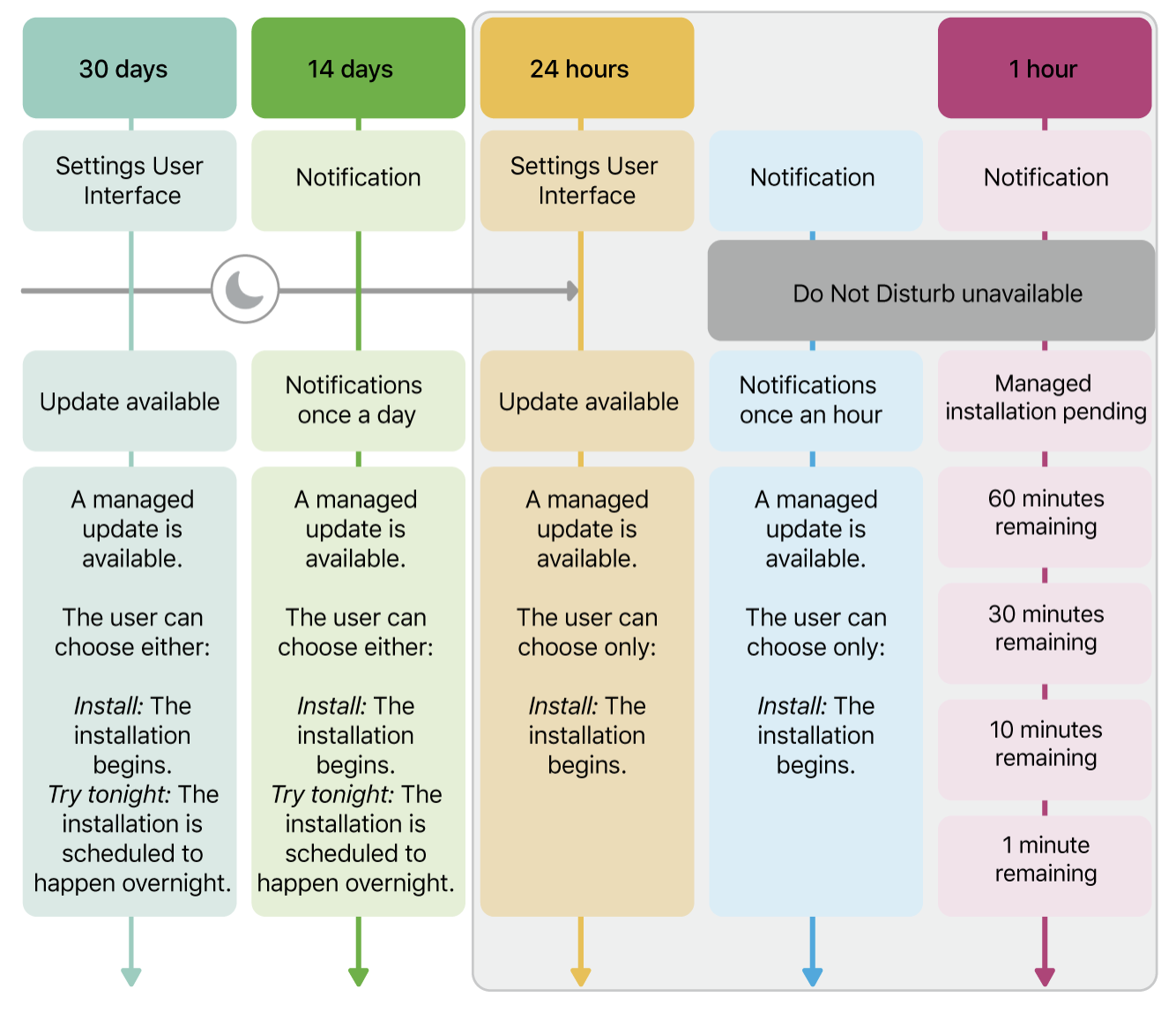
From 30 days until 14 days before the deadline, users receive one notification during that period, with the options to Install or Try Tonight. Between 14 days and 24 hours before the deadline, a notification is shown once per day. In the final 24-hour window, notifications appear every hour, and the only option presented is Install—the “Try Tonight” option is no longer available. These notifications bypass Do Not Disturb to ensure they’re seen. During the final hour, users are notified at 60, 30, 10, and 1 minute intervals as the update enforcement approaches. In the last 10 seconds, a countdown appears on screen before the device automatically restarts and begins installing the update.

Conclusion
Enforcing the latest iOS updates automatically with Declarative Device Management offers a modern, predictable, and scalable solution to a long-standing challenge in device management. By leveraging Intune’s support for DDM, IT can declare a delay-based enforcement policy that ensures devices update within a defined timeframe.
If you’re managing supervised iOS devices with Intune, now is the time to start using DDM to enforce the latest version across your fleet. It provides the balance between control and user experience—keeping devices secure and up to date, while giving users fair warning and time to act. Start testing, define your delay strategy, and move toward a more streamlined update experience.





.jpg)
.png)
