
Intune
Use Cloud PKI with Intune - Part 1: Setting Up PKI Infrastructure
By
This is some text inside of a div block.

In today's increasingly digital and security-conscious world, managing certificates for device authentication and encryption is essential. Microsoft's Intune Suite has introduced Cloud Public Key Infrastructure (PKI), which streamlines and simplifies the deployment of client certificates across your organization. Cloud PKI allows you to automate certificate issuance, scaling easily while reducing the complexity associated with managing traditional on-premises PKI systems.
Introduction: Simplifying Certificate Management with Cloud PKI in Intune
In this post, we will set up a complete PKI infrastructure, including a Root CA, Issuing CA (also called an Intermediate CA), and SCEP (or Microsoft’s SCEP solution, NDES). Setting up and maintaining this infrastructure traditionally requires significant effort and specialized knowledge, but with Cloud PKI, we can accomplish the entire process here. While Cloud PKI comes at a price, its capabilities make it a highly valuable solution for managing certificates securely and efficiently.
Quick Overview of PKI
Public Key Infrastructure (PKI) is a framework for managing digital certificates and public-key encryption, enabling secure communication and authentication. The Root Certificate Authority (Root CA) is the top authority that establishes trust by signing and validating certificates. Subordinate to the Root CA, the Issuing Certificate Authority (Issuing CA) is responsible for issuing certificates to end-users or devices. This hierarchical structure ensures both security and scalability in certificate management.
Root CA
- We begin by setting up the Root CA. Navigate to the Intune Admin Center > Tenant Admin > Cloud PKI, and click on Create.
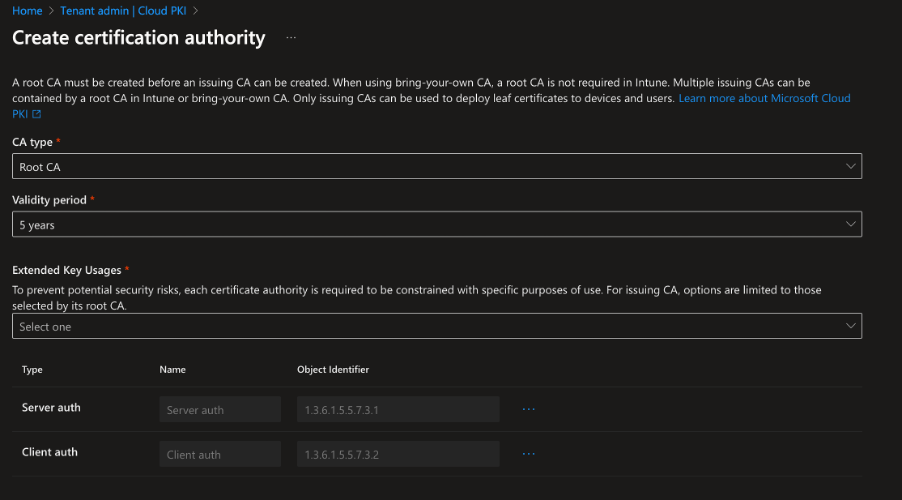
- Give your Root CA a name and configure it. The validity period of your Root CA determines the validity of your Issuing CA, with the lifetime of the Issuing CA limited to one year less than the Root.
For Extended Key Usage (EKU), choose the intended purposes for this Root CA, as the Issuing CAs will only be able to issue certificates with the selected purposes. Most common scenario is Client auth (so authentication pruposes from client devices for example for WiFi) or Server auth (when a server component needs to authenticate). The Common Name (CN) should clearly represent the Root CA’s identity to avoid confusion, especially in large infrastructures.
The CN should be descriptive and unique, such as "Infi Corp Root CA", to avoid ambiguity with other CAs or services.
- Although fields like OU (Organizational Unit) and Country are not required, it's best practice to fill them in for compliance and identification purposes. Ensuring these fields are correctly populated to align with RFC 5280, the PKI specification.
The key size determines the balance between security and performance. While 2048-bit RSA is strong for most use cases, you can opt for a larger key size (e.g., 4096-bit RSA) for heightened security. For specialized needs, creating a separate Root CA with a larger key size is a good option.
Once configured, you can create the Root CA. A summary of the configuration will be displayed for review.
Issuing CA
Next, we set up the Issuing CA, which will issue client certificates. To create the Issuing CA, go to Intune Admin Center > Tenant Admin > Cloud PKI, and click on Create. Fill in the name and select Issuing CA as the CA type, linking it to the previously created Root CA. The validity period for the Issuing CA can be up to one year less than the Root CA.
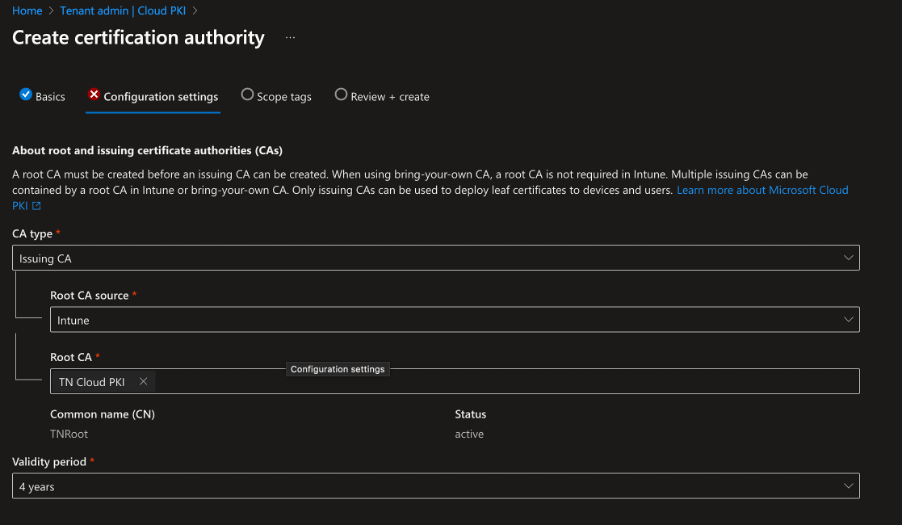
The Extended Key Usage (EKU) options are restricted to those chosen for the Root CA. Provide the Common Name (CN) for the Issuing CA, along with other optional attributes. After reviewing the summary, create the Issuing CA.
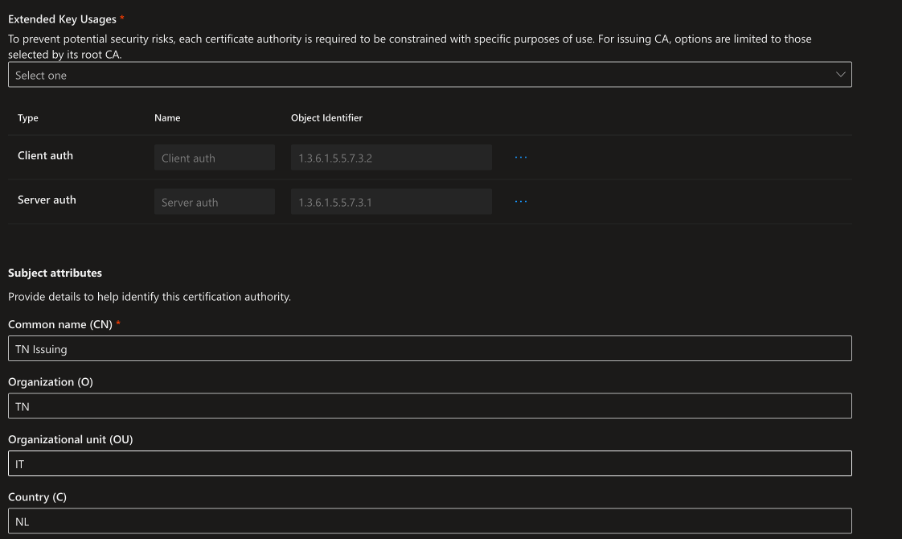
You will now see a summary of your IssuingCA. Go ahead and create this CA.
Setting Up NDES (SCEP)
NDES (Network Device Enrollment Service) or SCEP (Simple Certificate Enrollment Protocol) is the mechanism through which client devices (like Windows laptops or iPhones) request and receive certificates. The beauty of setting up the Issuing CA is that NDES is automatically configured during this process.

You can find the SCEP settings in the SCEP URI field in the Intune Admin Center. This setup enables devices to receive certificates that can be used for authentication purposes.
Conclusion
In this post, we’ve successfully created the foundation of our Cloud PKI infrastructure, consisting of the Root CA, Issuing CA, and NDES. The setup process is quick and simple, especially with Cloud PKI. In the next post, we’ll walk through configuring the remaining components to ensure client devices receive the necessary certificates for authentication.






.png)
